An interesting article and opinion was published today on Linkedin regarding BYOD, CyberSecurity and GDPR concerns
Mary Shacklett · March 5, 2019, 6:28 AM PST
Where trouble brews
But now some companies are discovering that BYOD causes more problems than solutions. Companies found employees were more likely to use their own mobile devices to grant credentials and issued their credentials to, say, online dating apps, which were not monitored by the company. Further, major liability risks occurred when employees accessed third parties with malicious intent making them victims of phishing and security breach schemes. All of the above can lead to stolen customer information, stolen intellectual property, and security intrusions that can bring down an entire corporate network.
Another reason for BYOD backtracking is the implementation of GDPR in Europe, which focuses on the information privacy rights of individuals.
However, a comprehensive yet easy-to-deploy solution is readily available.
Actifile (www.actifile.com) solutions resolve most of the BYOD challenges.
SECURING DATA USAGE ON ZERO TRUST DEVICES
Enabling employees, contractors and business partners,
to securely use corporate data taken from any application,
in a perimeter-less world
As organizations move more applications to the cloud and employ remote workers and 3rd parties using zero trust devices, they lose data visibility and control outside the applications.
Actifile’s unique low footprint technology enables employees, contractors and business partners, to securely use corporate data taken from any application or data source, whether or not the organization manages these applications.
Read More
The Challenge
The move to cloud applications and services has eliminated perimeter security that helped organizations control data. In addition, the explosive growth of the Gig Economy (the use of contingent workforce, 3rd parties and subcontractors) and the increase in remote work, have created more and more zero trust devices and BYOD, which are blind spots to current data control solutions. To secure data stored in the cloud, new products like CASB (Cloud Access Secure Broker) have been developed to enable control over application access and protect sensitive data when stored in the cloud. These products do not, however, cover users’ growing need to retrieve, process, store locally and distribute data pulled out of cloud applications, as part of their normal work routines. Once data is retrieved, the cloud controls are not effective anymore, which in turn creates a gap in data governance. The challenge is even bigger when data is pulled from applications that are not managed by the organizations (such as government and service provider repositories). Organizations may remain fully liable for information extracted from some of these repositories.
Additional challenge stems from the need to strike the right balance between users’ productivity and data privacy: corporate and zero trust devices contain a mixture of personal and organizational data that are hard to distinguish.
Actifile Guardrail Solution
Effective Approach to Protecting Data Outside Applications
Actifile addresses the challenge of securing data usage on zero trust devices by:
- Measuring the liability associated with company data stored locally or transferred to external clouds or other users.
- Transparently securing the company data when stored locally (for both transient or longer-term storage) or when transferred to untrusted clouds and/or recipients.
- Providing liability reducing controls such as remote wipe to address excessive risk, lost endpoints and/or employee turnover.
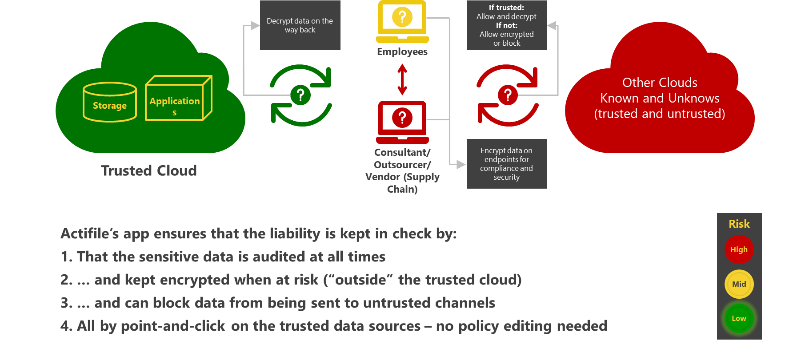
Actifile’s approach to securing data outside trusted applications has three pillars: Data Sources/Targets, Devices and Usage.
Source & Target Centric: The easiest way to protect data retrieved from applications, is to define the applications as the data sources and apply the appropriate controls by default to any retrieved data. In similar fashion, by defining the target applications as data targets, Actifile can control data flow to any target. Actifile supports both cloud-based and local applications and can protect data retrieved from sources such as: business apps, web portals, local apps, databases, code repositories and more. Actifile is focused on the data source and is agnostic to the tool used to retrieve the data, for instance using Excel to retrieve customer data from Salesforce. Actifile does not require configuration on the application side and can thus support applications outside of the organization’s control.
Given a user has access to an application, Actifile will handle any data retrieved from that app.
Usage Centric: to properly control data pulled from applications, requires supporting all potential user actions. Actions include data retrieval, with download, extract and copy & paste, data processing with merge or save as, data storage locally and data distribution (beyond the endpoint) to external repositories. Actifile’s solution is file agnostic, and protects any files types, such as: standard office 365 and G Suite, all pictures format like PNG and JPEG, Drawings like Visio and Autodesk, etc.
Device Centric: The organizational supply chain today combines full time and part time employees, subcontractors and business partners. When coupled with the increase in remote work, and the desire to balance work and life, has resulted in the proliferation of mixed-use endpoints, with a mix of personal and corporate data. Actifile patented container-less data separation method, insures that your organizational data is protected on one hand, and users and other organizations privacy is not tempered.
Actifile Guardrail Solution Benefits
- Reduces liability: Addresses the liabilities created by data that is outside trusted applications, in all transient states.
- Helps leverage the gig-economy: Work securely and productively with all types of employees including those who work outside of the organization
- Helps addresses the insider threats: Solve the problem of employee hoarding and carelessness.
- Gain visibility: of your sensitive data, outside applications.
Actifile Guardrail Advantages
- Zero Trust: Work in unmanaged endpoints outside your secured perimeter
- Zero configuration: Just and click on data sources to discover and protect
- Non-intrusive: Actifile has no effect on the corporate and users’ way-of-doing-business. Users continue working with their favorite application, while Actifile Guardrail transparently works in the background.
- Data and Application Agnostic: Works with any data taken from any application, cloud, on premise or local one.
- Ownership requirements: Protects also data you are liable for but do not technically manage, such as government repositories or online financial services.
- Easy to deploy and use: Does not require data security expertise to configure and maintain.
- Independent of network services: Active Directory not required.
- Supports offline mode: protection rules are persistent, even if the connection to the management module is disconnected.
How Actifile Guardrail Works

Actifile Guardrail is a lightweight application (<15 MB), is installed locally on the device (can be installed using automatic deployment tools) and managed using a cloud SaaS based module. Small footprint policies allow tether-less functionality (does not require directory integration), and SSO integration alleviates the need for policy writing. Actifile differentiates corporate data from other data, monitors select corporate data sources (cloud, intranet and applications) for sensitive data, tracks the sensitive data as it is used by different applications, uses an inheritance function to persist even when data is shared out-of-band. In addition, Actifile Guardrail uses transparent encryption, to secure the data without changing the way the users work with the data.

